In an April 2018 Strategic Finance article called “Cyber CFO: The Next Top Finance Job?”, I concluded that CFOs must head their companies’ cyber-risk management strategies because of potentially devastating exposure to cyberattacks and in response to the evolving regulatory and audit environment that’s driving changes in reporting and disclosure around the world. Yet when it comes to keeping up with or staying ahead of attackers in 2019, CFOs and their companies are struggling to tread water in what appears to be a tsunami of cybercrimes.
SKYROCKETING STATS
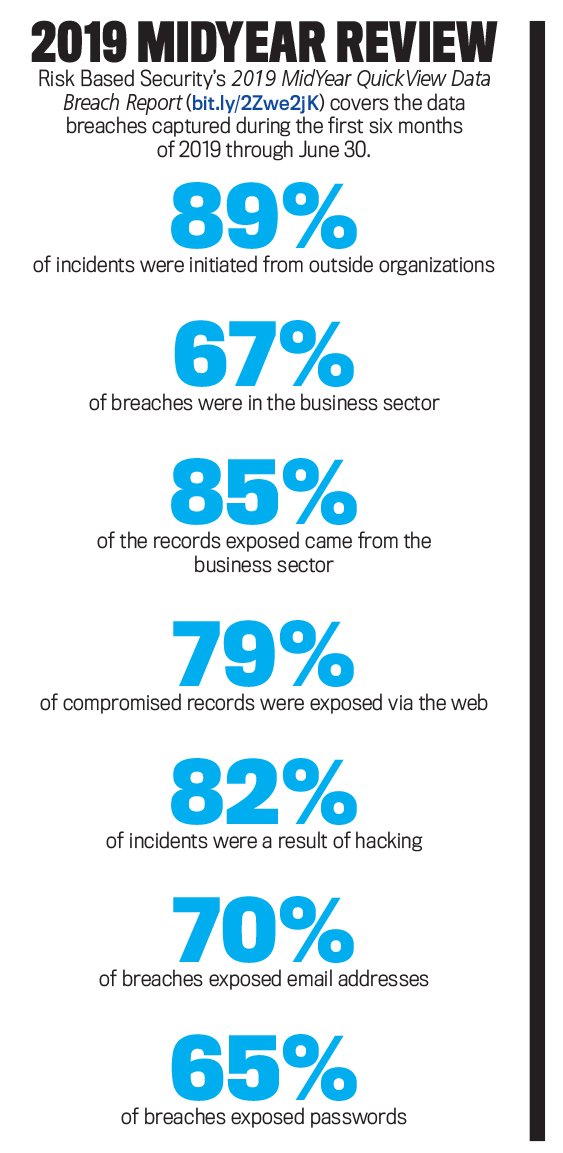
Just in the last year, the number of reported breaches was up 54%, and the number of exposed personal records was up by 52%, says Risk Based Security, a cyber protection and research company. According to its newly published research on the topic, 2019 MidYear QuickView Data Breach Report, there were more than 3,800 publicly disclosed breaches exposing 4.1 billion personal records in the first six months of 2019.
Of the breached organizations that could be definitively classified, Risk Based Security reports, the business sector accounted for 67% of reported breaches, followed by medical (14%), government (12%), and education (7%). This continues the trend observed in the Q1 2019 report.
According to Risk Based Security’s midyear report, the web remains the top source of breaches in terms of the number of records exposed, accounting for 79% of compromised records, while hacking remains the top breach type for number of incidents, accounting for 82% of reported breaches. Email addresses and passwords were primary targets, with email addresses exposed in 70% of reported breaches and passwords exposed in approximately 65% of reported breaches. These breaches affected all sectors of the economy.
FINANCIAL CONSEQUENCES
The impact on the bottom line is significant. On July 23, 2019, IBM Security announced the results of its annual survey examining the financial impact of data breaches on organizations. According to the report, the cost of a data breach rose by 12% over the past five years and now costs companies $3.92 million each on average. The financial consequences of a data breach can be particularly acute for small and midsize businesses, IBM reports. Companies with fewer than 500 employees suffered losses of more than $2.5 million on average (ibm.co/2jVhCRC).
And this isn’t a onetime hit. The report found that while an average of 67% of data breach costs were realized within the first year after a breach, 22% accrued in the second year, and 11% were realized more than two years after a breach. Healthcare, financial services, energy, and pharmaceuticals were hardest hit in the second and third years.
In addition, protection costs are on the rise. For example, reinsurer Munich Re estimates that the market for cyber-risk insurance could reach $8 billion to $9 billion in premiums by 2020, which is double the amount of premiums written just two years earlier (bit.ly/2lC5x48).
2019 HEADLINES
The statistics alone are startling, but the stories behind the numbers are even more concerning. Here are just some of the latest breaches and frauds to make news this year:
FIRST AMERICAN FINANCIAL CORP. DATA EXPOSURE. Improperly stored data resulted in the exposure of 885 million sensitive customer financial records as far back as 2003. Personal information up for grabs included Social Security numbers, driver’s license images, bank account numbers and statements, mortgage and tax documents, and wire transaction receipts.
EQUIFAX BREACH AFTERMATH. Equifax was charged $700 million to settle a series of state and federal investigations as a result of the massive 2017 data breach that left more than 147 million Americans’ Social Security numbers, credit card details, and other sensitive information exposed.
AMCA MEDICAL RECORDS BREACH. In June 2019, the American Medical Collection Agency (AMCA), a healthcare-related debt collector, reported that more than 17 million medical records were exposed. The compromised information included first and last names, dates of birth, phone numbers, addresses, dates of medical services, healthcare providers, and data on balances due. Risk Based Security notes that the fallout has been substantial. Clients severed their relationship with AMCA, consumer lawsuits were filed within days of the initial breach disclosure, and AMCA was forced into filing for bankruptcy protection two weeks after news of the breach made headlines.
CAPITAL ONE HACK. In the largest hack to date, more than 100 million Capital One customer accounts and credit card applications were accessed in late July 2019. Estimates suggest that 140,000 Social Security numbers, one million Canadian Social Insurance numbers, and 80,000 bank account numbers are at risk. A former Amazon Web Services software engineer was arrested.
LOCKERGOGA RANSOMWARE. LockerGoga is a newly discovered malware that extorts payment from industrial companies by promising to shut down computers that control actual physical equipment.
YAHOO PAYMENTS. Yahoo data breaches affected roughly three billion accounts from 2013 to 2016, and now the company has agreed to pay $117 million in a class action settlement. Verizon, owners of Yahoo, will spend $306 million between 2019 and 2022 on information security, five times what Yahoo spent from 2013 to 2016. These incidents show how hackers are getting into company databases and computer systems directly. Yet others are attacking even weaker lines of defense: the less-protected front lines of companies’ purchase-to-pay processes. Indeed, in terms of risk, supply chain is an open wound.
RISKS OF SUPPLY CHAIN AND CLOUD COMPUTING
Hackers are increasingly clever when it comes to infiltrating companies’ procurement-to-pay processes. In October 2018, the U.S. Securities & Exchange Commission (SEC) Enforcement Division released its report Regarding Certain Cyber-Related Frauds Perpetrated Against Public Companies and Related Internal Accounting Controls Requirements, demonstrating the extent to which cyberattackers are finding weaknesses in procurement and supply chain management processes.
In the instances the Enforcement Division reviewed, hackers accessed vendors’ email accounts and inserted fraudulent requests for payments (and payment processing details) into electronic communications. According to the report, the perpetrators of these scams also corresponded with personnel responsible for procurement so that they could gain access to information about actual purchase orders and invoices. Then they requested changes to the vendors’ banking information and attached doctored invoices reflecting new information.
Personnel responsible for procurement then relayed that information to the accounting personnel responsible for maintaining vendor data. As a result, companies made payments on outstanding invoices to foreign fraudulent accounts rather than to the accounts of the real vendors. The frauds continued over several months and in certain circumstances were detected only when the real vendors raised concerns about nonpayment on outstanding invoices (bit.ly/2kgBWNK).
While cloud computing may have benefits for some, the associated risks can be high. Companies lose control over their data, while the backlash of a cyber breach on their data remains with them. According to PwC, over the last three years, Operation Cloud Hopper, as it’s called (or Chinese-based APT10), attacked IT-managed service providers to gain access to data and networks in 15 countries (pwc.to/2m2LEnl). In 2019, the U.K.’s National Cyber Security Centre (NCSC) highlighted that a large number of organizations leave data unprotected in cloud storage locations such as Amazon S3 (bit.ly/2k1flEv).
ENTER THE AUDITORS
These are just a few examples of attacks that have wide-ranging impacts. It’s therefore no surprise that most companies are worried about their state of cyber readiness, how to tackle the growing threat, and what their new disclosure landscape will look like. For CFOs and their boards, the job isn’t only a technology challenge, but it’s one of operational and financial risk management. And the auditors will be keeping an even closer eye on them.
According to a May 2019 speech by Kathleen Hamm, a Public Company Accounting Oversight Board (PCAOB) board member, auditors should be looking more deeply into companies’ cyber-risk exposure and the controls in place to minimize cyberattacks. Her recommendations translate into a new agenda for auditors and for companies’ risk management and control practices (bit.ly/2m4s8qg).
The following is a list of potential questions that CFOs may be asked by their auditors in the near future:
- What are the methods your company uses to prevent and detect cyber incidents that could have a material effect on the financial statements?
- What processes does your company use to block and identify attempted unauthorized transactions or access to assets, and what is employees’ level of familiarity with those processes?
- What are the processes your company uses to assess and address material cyber incidents once they are identified? For example, this includes understanding how the company ensures timely evaluation and reporting of material cyber incidents up the management ladder.
- How does your company ensure appropriate escalation to the board and timely consideration of disclosure obligations to investors and others?
- Have you assessed the vulnerability of a company’s systems or subsystems that support the financial reporting process?
- What is the expected effect of a breach on your company’s operations and the financial implications? (The financial effects could include the loss of revenue from disrupted operations and the costs associated with securing, reconfiguring, and replacing systems. Costs also could include the fees associated with conducting forensic inquiries and defending the company against enforcement investigations and civil actions, as well as the payment of regulatory fines and monetary penalties to harmed private parties.)
- Did the incident result from a deficiency in your company’s internal controls over financial reporting, and have you put procedures in place to prevent similar future incidents?
- What are the nature and type of disclosures that your company is considering in its financial statements or the notes to those statements?
- When a cyber incident may appear not to be material to the financial statements, is your audit committee adequately informed as soon as it’s practical to do so?
MORE WORK TO BE DONE
In May 2019, ACCA (Association of Chartered Certified Accountants) published Cyber and the CFO, its report on cybersecurity and its implications for the finance function. The report is based on more than 1,500 survey responses and interviews with ACCA members around the globe. Given what’s at stake, the results are concerning.
The study concludes that in the event of an attack, the CFO will be accountable to shareholders and will be expected to provide accurate assessments of the potential damage, as well as lead both internal and external actions and communications. Yet the research also shows a troubling disconnect between who owns the financial and operational risk of the organization and where accountability lies for managing cyber risk.
Forty-four percent of survey respondents indicated the strategic direction for cybersecurity was set by the IT community—a combination of chief information security officer (CISO), chief information officer (CIO), IT manager, and chief data officer (CDO). In only 8% of respondent organizations did accountability rest with the CFO.
At the same time, knowledge of cyber risk was questionable. Forty-six percent of respondents said their last cyberattack was within the last year, 21% said they had never had one, and 33% didn’t know. Also, recovering from a cyberattack wasn’t high on the agenda. Just 32% said they have a remediation plan in place that’s updated and tested frequently to manage the impacts of a successful cyberattack, and 47% were unsure, don’t have such a plan, don’t test, or simply don’t know whether one exists. At the same time, an overwhelming 83% of respondents said their companies didn’t have cyber insurance.
TAKING ACTION
Accountants and finance professionals must play a leading role in creating a strategic approach to mitigating cybercrime risks. Management accountants must closely follow the work of governments and various regulators in order to have clear, up-to-date information about relevant legislation and requirements for adequate disclosure and prompt investigation of cybersecurity breaches.
They must define a risk management strategy and help their businesses establish priorities for their most valuable digital resources while also playing a leading role in creating reasonable estimates of the financial impact of cybersecurity breaches. And the finance chief must lead the charge in ensuring company data is safe and that investors are well informed about any risks related to cyberattacks and data security.
Finally, as ACCA says, CFOs and finance teams must also take a leading role in defending their organizations against cyberattacks. They must recognize that cyber technology presents a business and operational risk with a financial implication and can’t be left solely to the IT team. This includes understanding that the nature of cyber risk includes brand and reputational damage. And since cyber risk is a key component of the integrated supply chain, they must ensure that this risk is managed appropriately.
The ACCA report also notes that CFOs need to keep abreast of the changes in cyber threats, which are constantly evolving, and recognize that along with the currently known threats there are always unknown threats out there that have yet to be discovered. Cybersecurity is a commercial risk, and responsibility for managing it can’t be outsourced or delegated. That means CFOs will need to engage closely with IT professionals and develop a common language rather than seeing them as “the techies around the corner.” Even if they don’t become cybersecurity experts, CFOs need to ensure they aren’t managing only the risks they understand.
For the foreseeable future, CFOs will be involved in and probably leading initiatives against cybercrime. Data breaches and cyberattacks are on the rise and are now the No. 1 threat to the secure workings of industry and government. Stakeholders increasingly are demanding more transparency around cyber risk, and auditors are being encouraged to increase their scrutiny around how those risks are being managed, mitigated, and reported. As the caretakers of their companies’ assets, CFOs will be working even closer with their IT departments to ensure those assets are safeguarded.
© 2019 by Ramona Dzinkowski. For copies and reprints, contact the author.

October 2019