Internet of Things devices include everything from routers to security cameras and smart speakers in the home, and IoT Analytics estimates there are about seven billion internet-connected devices in 2019. The method used by Kaspersky to catch and track the smart device attacks involved setting digital traps called honeypots, more than 50 deployed around the world to track the 20,000 infected sessions appearing every 15 minutes.
The press release notes that the new total is almost nine times greater than the number found in H1 2018. Last year, about 12 million attacks were identified in H1, originating from 69,000 different IP addresses. Two contributing factors for the increase are the fact that IoT devices can be easier to hack than more sophisticated systems, and that the ways to monetize the effort are flowering.
The report explains how the majority of attacks download the most popular malware families like Mirai (responsible for 39% of attacks) and Nyadrop (seen in 38.57% of attacks). The Mirai malware makes network devices convert to remotely controlled bots to be used in massive numbers for large-scale network attacks. The Nyadrop malware is a Linux Trojan used as a tool to load other malware.
HONEYPOTS
Wikipedia describes a digital honeypot as “a computer security mechanism set to detect, deflect, or, in some manner to counteract attempts at unauthorized use of information systems.” The honeypot is data that looks like it’s part of the device’s or network’s code, when actually it’s isolated and constantly monitored.
It can be designed to look like something valuable to the attacker. Once the attack is detected, the honeypot tracks the attacker’s information, including the location of its source. The trap blocks the malware’s efforts by isolating its code and operations from the rest of the system.
A typical placement in the system can look like this:
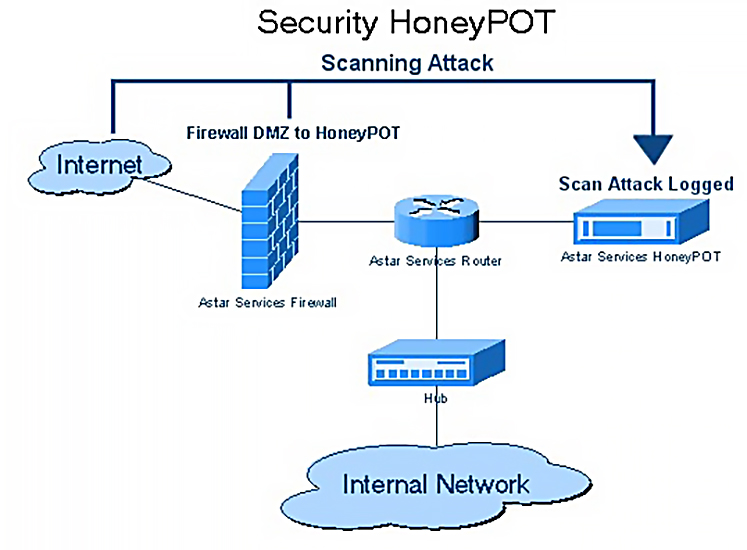
Honeypot diagram from Wikipedia Commons
Along with the numbers and kinds of attacks, the honeypot logs the location of the attackers, and although these numbers change often, the current list of countries in the top five hacker locations includes China, Brazil, Egypt, Russia, and the United States.
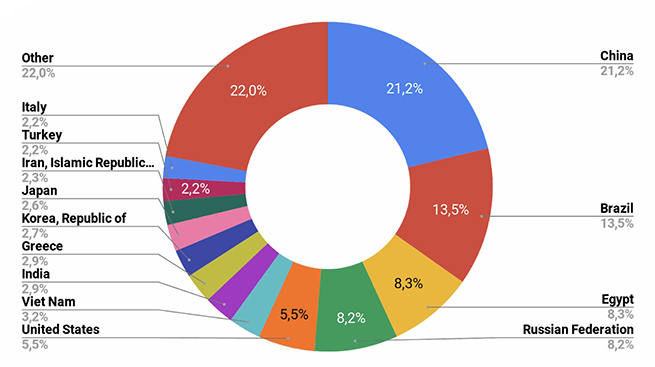
Graphic from Kaspersky Lab
RECOMMENDATIONS
Kaspersky offers two lists of advice for individuals and companies to avoid what’s becoming an ever-increasing wave of attacks coming from around the globe.
To keep your devices safe, the Kaspersky Lab suggests that users:
- Install updates for the hardware you use as soon as you are notified of their availability.
- Always change preinstalled passwords. Use complicated passwords that include uppercase and lowercase letters, numbers, and symbols.
- Reboot a device as soon as you think it’s acting strangely. Keep in mind, however, that this might help get rid of existing malware, but it doesn’t reduce the risk of getting another infection.
- Keep access to IoT devices restricted by a local VPN (virtual private network), allowing you to access them from your home network, instead of publicly exposing them on the internet.
For companies, the cybersecurity firm suggests:
- Use threat data feeds to block network connections originating from malicious network addresses detected by security researchers.
- Make sure all device software is up to date. Unpatched devices should be kept in a separate network inaccessible by unauthorized users.
(The full text of the Kaspersky report, IoT: a malware story, can be read on the Securelist website .



