A recent case for computer pocket keys in the form of USB sticks was announced by Microsoft on Tuesday, November 20, 2018, to its 800+ million users of Office 365, One Drive cloud, Outlook, Bing, Skype, and Xbox Live. Hardware authentication keys will eliminate the need for passwords for these programs that are running on the new Windows 10 and the Edge browser.
Microsoft explained that its no-password login system would use FIDO2-compliant hardware keys. The effort has been a long-range project for the company, and in September 2018, Rob Lefferts, vice president for Microsoft Security, announced in a blog post, “We are declaring an end to the era of passwords.” Lefferts offered reasons for the change. “Passwords are…bad for people. They’re the easiest way for attackers to get in, and in the case of account takeovers, they’re even a way to force people out.”
The list of inherent weaknesses in traditional passwords is long. The better the password, the harder it is to remember. The common-sense rule that you shouldn’t use the same password can lead to an overload. One estimate from Shacknews asserts the average worker has more than 100 passwords to maintain, both work-related and personal.
Password managers can help, but they also introduce an additional level of risk, offering one-stop shopping for hackers looking for more than just one of your keys. Each increase in raw computing power diminishes the strength of your passwords, and the prospect of quantum computers offers the ultimate threat to passwords that we now consider uncrackable.
And finally, your password isn’t completely under your control. Yes, you have your copy, but the keeper of the locks that you’re trying to reach also has to recognize your key—they have a copy. For this reason, the first announcement that your online service has been hacked is usually followed by an urgent appeal to immediately change your password, which is now in three places—your computer, the service’s servers, and some character who will soon be hawking it to buyers in one the backrooms of the dark web.
A PASSWORDLESS FUTURE
Today you have several ways of signing on to programs and websites. Simple passwords can be used to log in (single-factor authentication), but the secrecy depends on your vigilance and those operating the servers that check and okay your information. A more secure method is two-factor authentication (2FA).
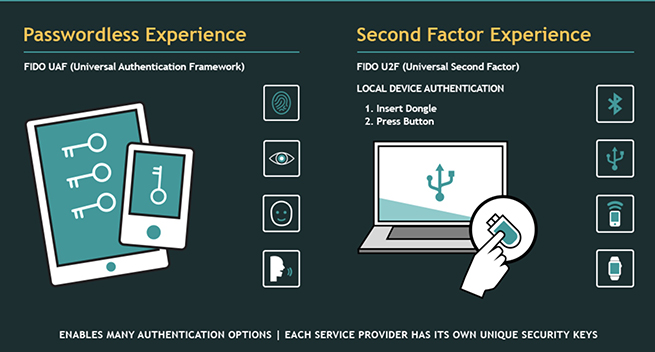
The new Microsoft system will work with several kinds of hardware key systems. All are based on the FIDO2 protocol. The FIDO (Fast Identity Online) Alliance is a tech consortium made up of more than 250 members from tech, retail, and banking sectors. Founded in 2013, and based in Mountain View, Calif., the group is dedicated to developing specifications they hope will become the standards for many authentication technologies, including biometrics, smart cards, near-field communication (NFC), and USB security tokens.
The 2FA that Microsoft is now encoding in many of its programs and platforms is FIDO2-compliant. In brief, here’s how the authentication process works:
2FA begins with a password or PIN—that’s called the knowledge factor—and then adds either a possession factor or an inherence factor. Possession could be in the form of an ID card, a security token, or a mobile device. Inherence refers to biometric factors, such as a fingerprint, or voice- or facial recognition. So, 2FA is a multifactor authentication that requires two factors from two different categories. Two factors from the same category wouldn’t qualify because that would be one-factor authentication. Here’s how the FIDO Alliance charts 2FA.
On the left is password or PIN (knowledge factor) plus inherence (fingerprint, retina, facial, or voice recognition). On the right is the mechanical key connected via Bluetooth, USB, and near-field communication (NFC), from mobiles like smartphones or watches).
What makes FIDO authentication stronger than conventional 2FA is that it’s “based on proven public-key cryptography where the private key (and biometric templates when used) is stored on—and never leaves—the user’s device.” To succeed, a hacker would have to find the location of and take possession of the hardware key from the user.
TYPES OF KEYS
The new implementation of passwordless sign-ins for the Microsoft products allows a two-step process to be simplified to a single-factor authentication. Once set up, you no longer need user name or password. Just plug in a key, like one of the YubiKey 5 from Yubico, and you’re logged in. Google, Facebook, Dropbox, Salesforce, and other services already allow FIDO key first- and second-authentication.
One of the most successful key providers for individuals and companies is Yubico (yubico.com) with its YubiKeys in a number of formats and styles. The Yubikey 5 series range in price from $20 to $60 per key, and the types include USB-A, USB-C, and NFC (near-field communication). On the website, there’s a quick search solution to help you find the right key from among the variety available to individuals, IT professionals, security experts, and a category called Government/FIPS.
Google also has the Titan Security Key ($50 for a set of two) that includes one USB key and one Bluetooth key.
https://www.youtube.com/watch?v=MHTIVR1mY7k
For a helpful walkthrough of how to set up and use a hardware key like the UbiKey, watch the YouTube “Yubikey 5.0—How to use a Yubikey & LastPass to Secure all your online Accounts!” It runs almost 20 minutes, but even if you don’t end up using UbiKey or LastPass, it’s a great introduction on how this kind of security can work for individuals or businesses.
Today, you’re likely to come across more security keys in enterprises than among individual users, but as hacking algorithms and hardware get stronger, initiatives like the one taken by Microsoft this month will doubtless accelerate the adoption of pocket keys for your devices.