From the hacker attack on the Oldsmar, Fla., water treatment facility to the SolarWinds attack that affected more than 18,000 entities, cybersecurity threats are widespread and unrelenting. Ransomware is a primary threat to the small to medium-sized entities that employ most of us. Once a ransomware attack is initiated against your company, it’s too late to act. Whether you pay the ransom or rebuild your databases, it will cost you time, disruption, and money.
Regulatory responsibilities are expanding with data protection and privacy laws. Finally, your business partners (customers/vendors) with whom you have spent time and money on systems integration are now sending you long questionnaires about your cybersecurity programs and how you’re protecting them. These risks and challenges affect many management accounting and finance professionals since corporate boards frequently place the IT functions and responsibilities under the leadership of the CFO or controller.
The National Institute of Standards and Technology (NIST) is a nonregulatory federal agency within the U.S. Department of Commerce with a mission to advance U.S. competitiveness through advancement of methods and standards including technology. The NIST’s Framework for Improving Critical Infrastructure Cybersecurity (often called the Cybersecurity Framework, or the CF) and related NIST publications are excellent resources to challenge and improve your organization’s cybersecurity controls presented in a way that management accountants will understand, given their background in process and controls. These materials are available free of charge and are updated via an ongoing collaborative effort involving industry, academia, and government.
CF IMPLEMENTATION
The CF is a broad framework inclusive of governance of IT, monitoring, configuration, detection, response, and recovery. It’s an excellent complement to the Committee of Sponsoring Organizations of the Treadway Commission (COSO) Internal Control—Integrated Framework many have already adopted. Using the CF, finance sets organizational standards, processes, and methods and collaborates with IT to interpret and actualize the detailed IT objectives and controls. Complementing the CF is Security and Privacy Controls for Information Systems and Organizations, which was updated in December 2020 and has a comprehensive catalog of security and privacy controls aimed at securing systems and data while also protecting personal identifiable information.
For most organizations, all these security and privacy controls classified as low baseline have a higher priority and should be in place before proceeding to those classified as medium or high baseline. The baselines are also helpful for assessing your program’s maturity.
The first step to implement the CF is to identify all IT planning and control activities occurring either internally or performed externally by business partners. These IT controls need to be assigned an identifying number and should include a comprehensive control description, a control owner, a frequency, and a step-by-step control procedure. Be sure to include Software-as-a-Service/Platform-as-a Service/Infrastructure-as-a-Service providers in gathering the controls listing. It’s important to coordinate with the main business contact with each to obtain a SOC 1 and/or SOC 2 report (System and Organization Controls Report), review the Complementary User Entity Controls (CUECs) in each report, ensure such controls take place in your organization, and “map” these controls to the CUEC or document-control gaps. Based on my experience, a midsize public or nonpublic entity will typically have 65 to 75 IT controls.
Figure 1: Control Coverage Assessment
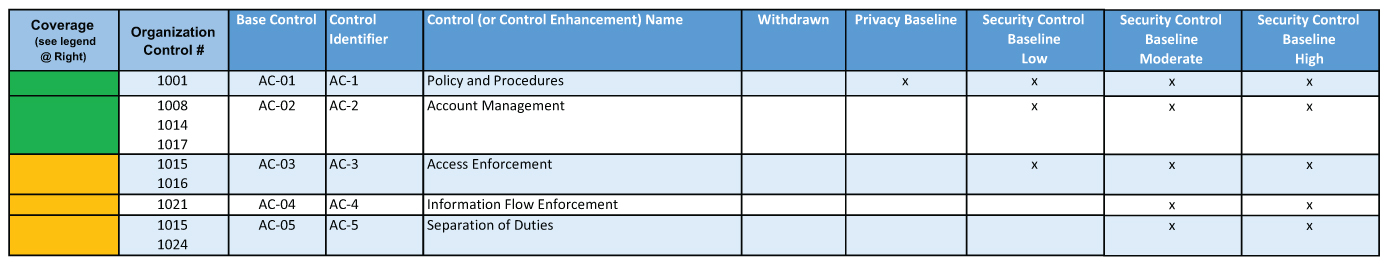
Next, “map” your controls to the base controls in the NIST controls catalog. NIST provides a downloadable Excel file to facilitate this mapping. Simply add columns for your control numbers and coverage assessment. Map to the base controls only (e.g., AC-2). Use the control enhancements (e.g., AC-2(1)) to assess the adequacy of the coverage for that base control, to inform enhancements to your existing controls, or to identify new controls to add. There are 322 base controls, so your controls should map to several of them.
Next, assess coverage as green (controls fully address base control), yellow (controls partially address), red (gap), or blue (base catalog control is not applicable to your organization). (See Figure 1.) Once gaps are identified, review the NIST control enhancements to inform the development of controls to mitigate the gaps, along with a realistic implementation time frame.
MAPPING CONTROLS
Once an updated control listing and implementation plan are developed, then map your controls to the CF. If you’re familiar with the COSO model and/or the Risk and Control Matrix frequently used to accumulate and document internal controls relative to risks, think of the NIST category as akin to the activity/outcome of COSO and the NIST subcategory as like a COSO objective. There’s no explicit risk element in the CF, so you’re mapping controls to the subcategory. Include all controls that are relevant to the objective expressed by the subcategory.
The result of mapping your controls is called your “current profile” CF. You can then draft your “target profile” CF in a separate file by adding the controls you developed to address the gaps identified during the mapping processes. Further review of this target profile with all stakeholders and consideration of the desired implementation tier as described in the CF may lead to identification of additional controls to implement. Develop an action plan for each upcoming year to improve your process to match the desired target profile within the time frame set by management.
Actualize this process in your organization by ensuring that there’s a detailed control procedure for each control. Use a workflow solution that can be as simple as an IT ticketing system. Using a ticketing system, for example, set up a folder for “controls execution,” create a ticket for each control, and route the tickets to the person performing the control for each time period due. They perform the control and attach supporting evidence of performance to the tickets, and the completed tickets are routed to the control owner for review and closure. In this way, you’ll make sure all controls are completed, or you’ll at least know which ones aren’t. These tickets will serve as evidence with electronic signatures that the control was performed and reviewed. We expect very few issues once control performance workflow is fully implemented. Review of the open tickets serves as ongoing follow-up and identifies any controls where the performer or the reviewer has left the company.
The CF is an excellent source for management accounting and finance professionals to challenge their organization to either formalize their cybersecurity process or to assess and improve existing processes. Implementing a widely adopted framework prepares your organization to respond to the inquires and requirements of your organization’s leadership and business partners and instills confidence that serious efforts are being implemented to protect stakeholders.

July 2021



