Hackers had a field day breaking into computer systems during the spring and summer of 2019. In May 2019, the City of Baltimore suffered a phishing ransomware attack, paralyzing the city’s IT services. Another ransomware attack shut down 23 state agencies across Texas during the same period. Don’t think it can’t happen to you.
Management accountants are on the front line of data governance to “ensure the availability, utility, integrity, and security of data” according to the IMA® (Institute of Management Accountants) enhanced Management Accounting Competency Framework. Let’s examine safeguards your organization can take to defend against the growing risk of cybersecurity attacks.
THE CYBERATTACH PLAYBOOK
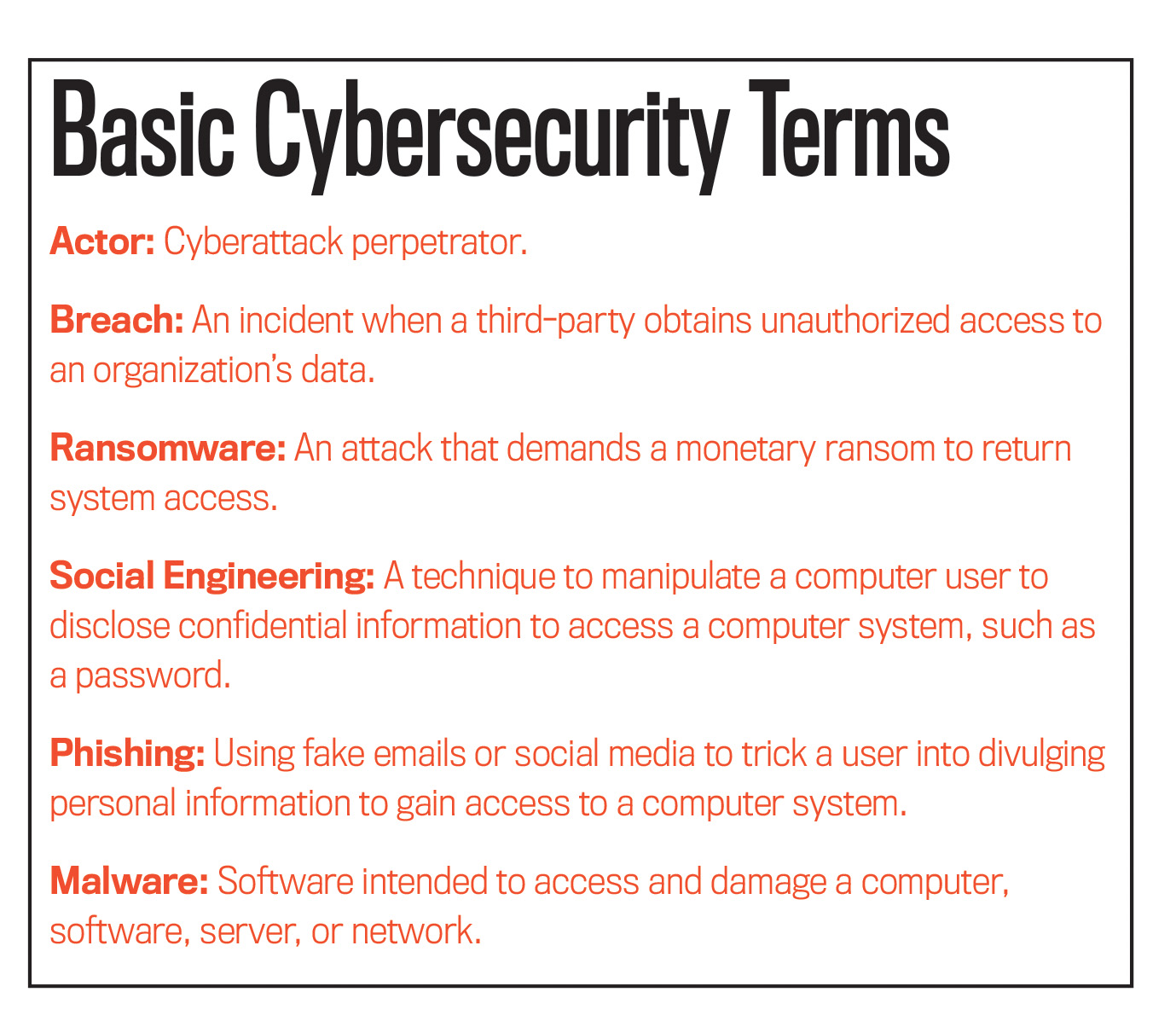
According to Verizon’s 2019 Data Breach Investigations Report (DBIR; vz.to/34fXxam), an annual report analyzing cybersecurity breaches, small businesses were the victims of 43% of cyberattacks out of 2,013 confirmed data breaches analyzed. Sixty-nine percent were perpetrated externally, 34% internally, and 23% by foreign nation-states, and 71% were financially motivated. A scary finding is that in 56% of the cases, discovering the attack took months. The most common type of attack was caused by hackers (52%) followed by social engineering (33%) and malware (28%). It’s time to get your finger on the pulse of the risks, exposures, and trends in the cyberattack playbook.
Forecasting the cost of a cybersecurity attack should be enough to get your attention to shore up your organization’s cybersecurity defenses. The Baltimore ransomware attackers demanded $80,000—the city refused to pay. The final recovery cost was estimated at $18 million. According to Target’s 2015 Form 10-K, 40 million customers’ credit and debit card data was stolen during a malware attack in late 2013, costing the company about $252 million in pretax earnings. Insurance coverage and tax deductions reduced the cost to about $105 million.
The first line of defense is to raise awareness throughout your organization about the risk of cyberattacks and what employees can do to avert the risk. Mandating employee cybersecurity training—at least annually—is imperative. Texas passed legislation requiring cybersecurity training for most state employees by June 2019, five months before the state’s cyberattacks. Robert Herjavec of Shark Tank fame and owner of a cybersecurity company says, “People, process—then technology—will address the greatest challenges we all face in cybersecurity.”
CONTINGENCY PLAN AND CYBERSECURITY POLICY
Thirty years ago, backup and recovery measures from a computer crash involved restoring data from a backup and marching on smartly. Downtime was limited to the time needed to restore the backup. Times have changed. Hackers can take control of your IT system and freeze it, denying all access, causing your business to come to a grinding halt. A small, private university in Denver, Colo., was the victim of a cyberattack in August 2019 at the beginning of the fall semester. Its entire IT infrastructure—website, phones, email, and computer system—was down for more than two weeks. Communication initially occurred through its Twitter account until a temporary website was built. The start of classes was delayed until the system was restored. Though no leader wants to see their organization fall victim to a cyberattack, it’s important to be prepared.
Because of the risk of losing your IT infrastructure, it’s imperative to have a disaster recovery plan to respond to the attack and restore your system and a business continuity management plan to continue to operate your business while you recover from an attack. The longer you’re out of action, the more expensive it will be in terms of lost revenue and reputational damage. You must develop a formal cybersecurity policy that includes how to deploy it. Even if the first version of the plan only says to disconnect the servers to halt the spread of the damage and call a forensic cybersecurity firm to investigate, that’s a step in the right direction. The more comprehensive the policy, the better. Just like your system of accounting internal controls, the policies must be tested for effectiveness. If you don’t know how to proceed, engage a cybersecurity consulting firm to develop, test, and audit your plan.
CYBERSECURITY INSURANCE: CAVEAT EMPTOR
The cost of recovering from a cybersecurity attack can be expensive, as noted in the Target example. One strategy for mitigating the risk of the cost of the attack is to purchase cybersecurity insurance. Allied Market Research forecasts that cybersecurity insurance will grow to $14 billion by 2022 primarily driven by the U.S. market. Insurance policies include premium cost, deductibles, and coverage exclusions limiting coverage.
But be careful: Make sure you understand the policy and the application process. Many insurance policies require completing a questionnaire asking questions about your business’ current cybersecurity policy. If you don’t have one, that’s your answer—you don’t have one. Beware of coverage exclusions. Foreign nation-state-sponsored cyberattacks, one of the biggest risks identified in Verizon’s DBIR, may be excluded. Also, social engineering attacks may not be covered since they indicate lax cybersecurity policies and could have been prevented by a cybersecurity policy and employee training.
Management accountants understand the adverse effect of risk on their companies and should be active participants in safeguarding their company’s data by participating in the development of internal controls and policies to prevent attacks. Cyberattacks are in the risk red zone and are on the rise. Don’t leave your company exposed. Acting tomorrow to defend against a cyberattack might be too late. It can happen to you today. The opinions included are those of the author and not necessarily those of the U.S. Air Force Academy, the U.S. Air Force, or any other federal agency.

December 2019


